Verizon finds companies relaxed mobile security policies to get employees online
Security was not a priority for many organizations as they rushed to get employees up and running a year ago, Verizon said, adding that this was especially true for mobile security ... According to the fourth annual Verizon Mobile Security Index, 45% of organizations sacrificed mobile security for expediency over the past year ... The Verizon Mobile Security Index is based on interviews with 865 business professionals located in the U.S., U.K., and Australia who are responsible for buying and managing mobile and IoT devices for their companies.
Join GamesBeat Summit 2021 this April 28-29. Register for a free or VIP pass today.
Security was not a priority for many organizations as they rushed to get employees up and running a year ago, Verizon said, adding that this was especially true for mobile security.
According to the fourth annual Verizon Mobile Security Index, 45% of organizations sacrificed mobile security for expediency over the past year. Interestingly, the number of organizations experiencing a compromise or breach dropped to 23% over the past year, a slight decrease from 27% in 2018. The Verizon Mobile Security Index is based on interviews with 865 business professionals located in the U.S., U.K., and Australia who are responsible for buying and managing mobile and IoT devices for their companies.
Cutting corners to cope
With VPN and Wi-Fi connectivity inconsistent and unreliable for many remote employees during the pandemic, mobile devices and cloud applications quickly became the go-to platforms for getting work done. IT teams are still under pressure to grant greater access privileges to less secure mobile devices, often operating on networks the company doesn’t own. IT supports a wider variety of remote workers than ever before, from commuters to road warriors in sales and service, putting more time pressures on them. Add all these factors together, and it’s easy to understand why mobile devices are the most vulnerable across the threat landscape today.
Approximately three-quarters of IT teams (76%) are being asked to relax security policies for mobile devices so employees can meet deadlines and achieve business goals. Verizon’s index reflects the conflicts IT teams face between protecting mobile assets and helping employees do their jobs. IT teams recognize that mobile devices pose significant risks to the organization: 40% named mobile devices as the biggest security risk and 50% said risks posed by mobile devices are growing faster than other risks.
Need to get basic protections right
As part of its Mobile Security Index, Verizon tracks how many companies have four basic protections: changing all default/vendor-supplied passwords; encrypting sensitive data when sent across open, public networks; restricting access to data on a need-to-know basis; and regularly testing security systems and processes. Even though these four items are considered security fundamentals, the Index found just 9% of organizations had all four in place this year, while the average from previous years was 12%. Almost half (49%) said they regularly tested security systems and processes, but just 39% said they regularly changed passwords or restricted data on a need-to-know basis. Even more worrying, 15% did not have any of these four protections in place.
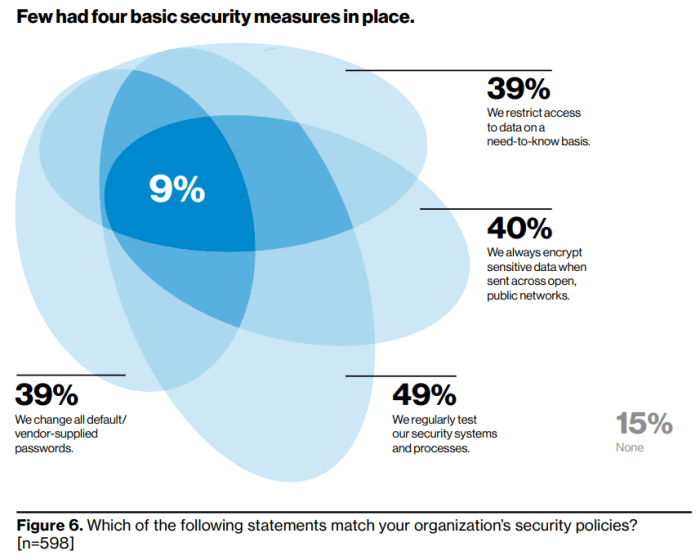
Above: Some organizations had one or more of the four basic protections, but few had all four.
The past year has been especially challenging for organizations relying on legacy trusted and untrusted domains to protect the rapidly growing number of mobile devices that needed to be mapped into domains. And this situation isn’t changing anytime soon. Organizations consequently need to treat identity as the new security perimeter and consider a data-centric security model to scale more effectively.
BYOD gets a second chance
The pandemic caught many organizations without enough laptops and tablet devices to outfit their workforce. There was also an acute laptop shortage, with lead times of 16 weeks or more for many models as manufacturers shut down and supply chains faced disruptions. The pressure points over the past year exposed some of the glaring security weaknesses organizations currently have. Too few are getting basic protections right, but the Verizon Mobile Security Index offers ways to improve.
Over the past year, 36% of organizations opened access to corporate resources and systems for employees using their own devices, according to Verizon. The Mobile Security Index tracks both BYOD (bring your own device) and BYOPC (bring your own PC), and it shows many organizations began considering BYOD and BYOPC as viable strategies this year. Over 25% of organizations reported already allowing BYOD, but fewer than 25% of organizations supported BYOPC.
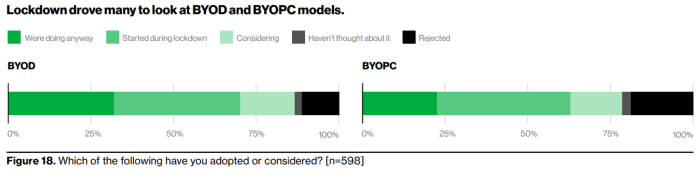
Above: Many companies started considering BYOD and BYOPC as a viable strategy.
A key element of BYOD and BYOPC strategies, or any kind of virtual work, is providing secure access to company applications, databases, and internal systems. If not done correctly, there is the risk of large-scale data breaches.
The Cybersecurity Framework from the National Institute of Standards and Technology (NIST) makes a strong case for zero trust frameworks for data-centric security in organizations relying on BYOD and BYOPC. Implementing a zero trust framework requires mobile device management (MDM) and unified endpoint management (UEM) to secure endpoints at scale. Having a UEM platform supporting BYOD and BYOPC devices helps ensure every endpoint can be self-diagnosed and self-remediating.
Leading providers of MDM and UEM solutions include Ivanti, Hexnode, ManageEngine, and Sophos. Identities are the new security perimeter and why zero trust in a mobile-first, cloud-first IT environment is a clear path forward.
VentureBeat
VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative technology and transact. Our site delivers essential information on data technologies and strategies to guide you as you lead your organizations. We invite you to become a member of our community, to access:- up-to-date information on the subjects of interest to you
- our newsletters
- gated thought-leader content and discounted access to our prized events, such as Transform 2021: Learn More
- networking features, and more